technology in the world.
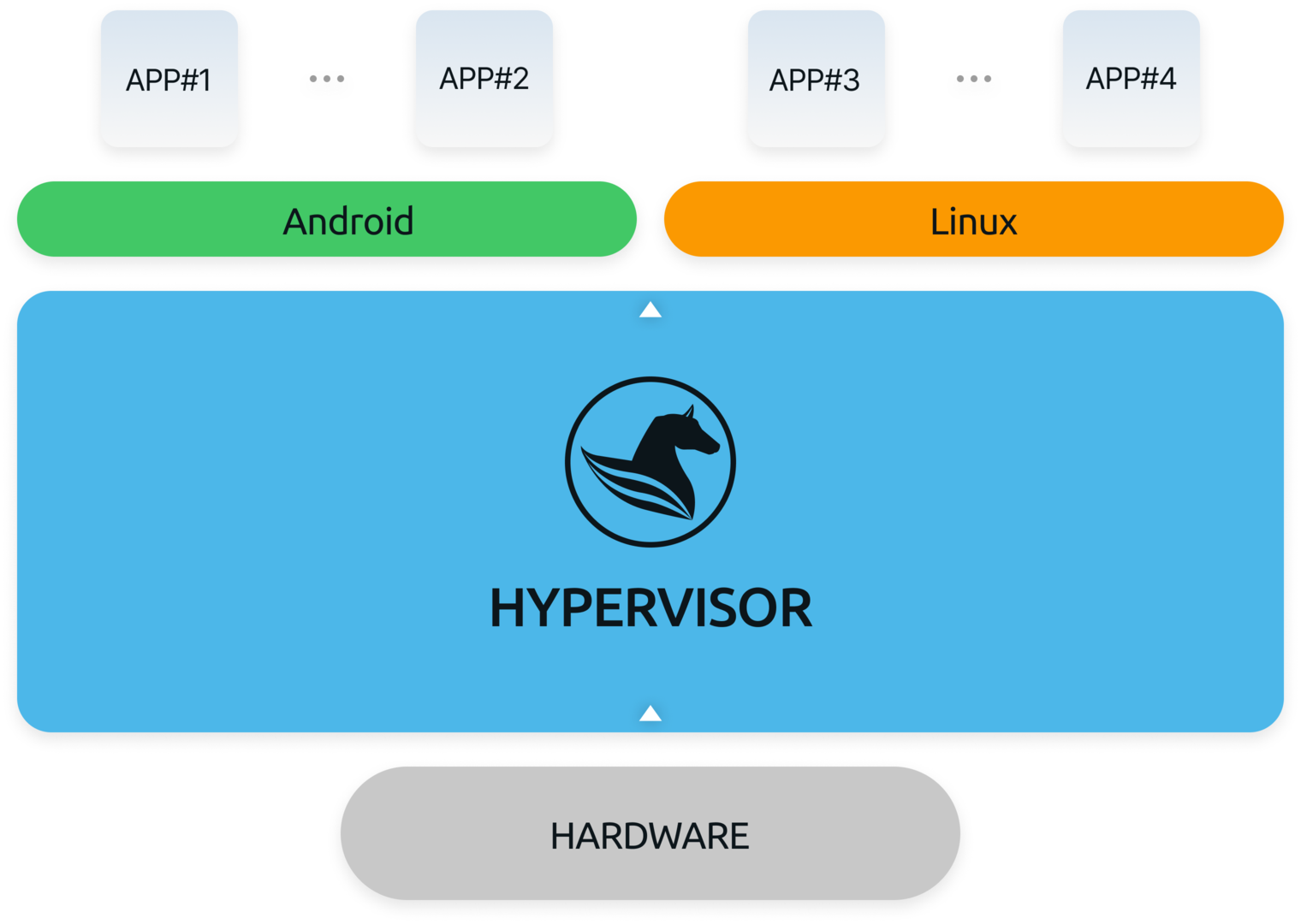
Hypervisor is software that takes computing resources such as a processor, memory, and storage from a computer device and reallocates them to virtual machines (VM).
This technology enables the creation of multiple virtual machines (VM), allowing multiple OS to run on a single computer device. It is amazing technology that turns a single physical computer device into multiple virtualized devices, all through software.
with the most stable architecture. At the same time, it has the longest history.
technical expertise, from architecture design to implementation. Check out the key technical features of PEGASUS.
-
Safe development languageRUST-based
developmentIt is developed using RUST, which offers superior stability
compared to traditional C and C++, thereby maximizing stability
and reliability.Supports multiple
coding languagesTo meet the diverse requirements of our customers, both C and C++ versions are also provided, ensuring compatibility across a wide range of environments. -
Efficient Virtualization TechnologyUtilizing VirtIO
technologyBy virtualizing device drivers with VirtIO technology, existing commercial OS can be used directly without the need for a separate hypervisor-specific OSApplication
CompatibilityIt is designed to run applications directly in existing OS environments, reducing the cost and time burden of system transition. -
Leading the way in hypervisor technologyMeister of
hypervisorBased on Perseus' core technology, 'Secure Xen ARM,' our hypervisor is developed entirely with Perseus' technology, covering architecture design, implementation, and development from the ground up.Tailored solution
for customersFeatures, performance, and specifications can be flexibly adjusted according to customer requests and are delivered with the most perfect and secure design in the market -
Mature hypervisor technologyExtensive mass
production
experienceDr. Suh, the founder of Perseus, is the founder and maintainer of 'Secure Xen Arm' since 2007. Additionally, with years of collaboration and experience with the Perseus team, he has extensive mass production experience.- As Development Lead (Senior Vice President) for Mobile OS, TIZEN at Samsung Electronics, he was responsible for overseeing open-source standard OS products and developing the hypervisor.
- Mass production experience with OS and hypervisor for mobile, wearables, and smart TVs on ARM cores
Support for
various
architecturesWe support both CPU (A-Core) and MCU chips (R-Core), as well as full-virtualization and para-virtualization.- A-Core
: It is optimized to run complex OS and Apps that require high performance. - R-Core
: Widely used in products requiring real-time data processing, such as vehicle electrical/electronic systems and robots.
-
Hypervisor
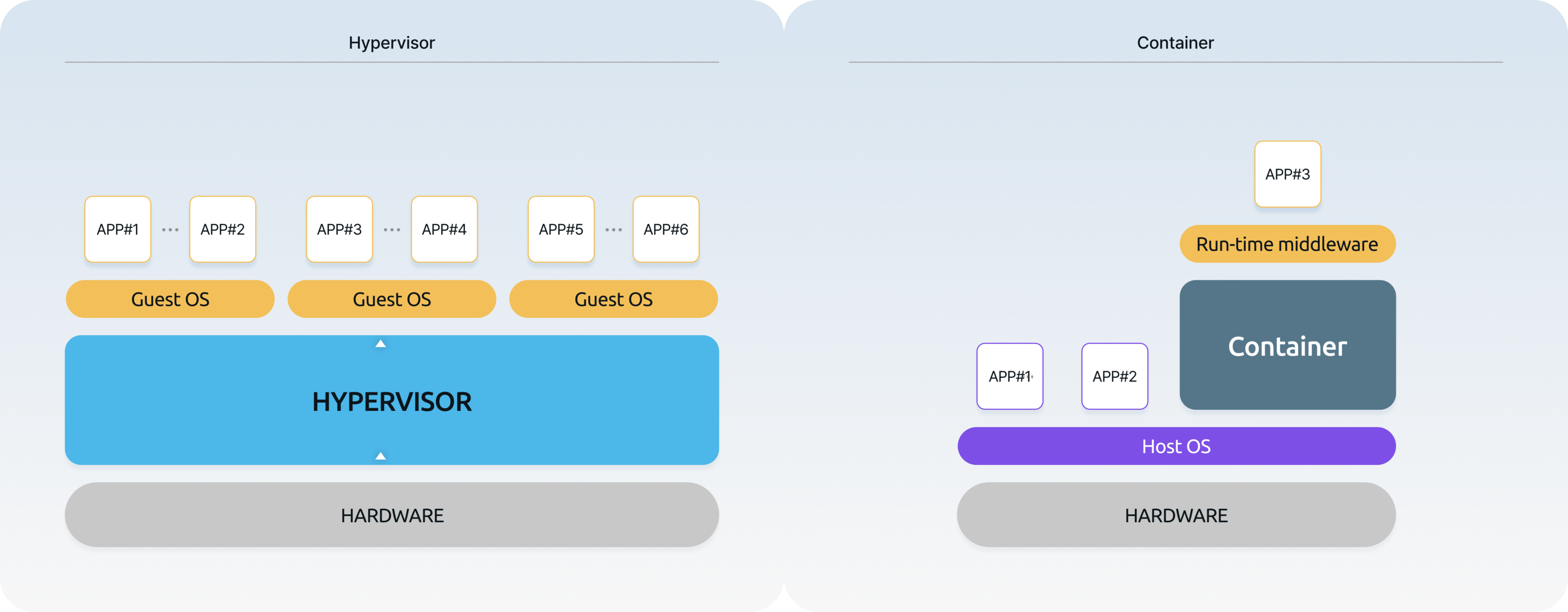
and ContainersIn the virtualization market, the main technologies are divided into hypervisors and containers. Currently, the market is primarily represented by servers, with hypervisors such as Xen and KVM while containers like Docker are widely utilized. -
HypervisorThe hypervisor runs directly on top of the HW, also known as bare metal. Thanks to this characteristic, the speed at which the HW resources are transferred to the VM is very fast, and the degree of freedom in the role that can be played between the HW and the OS is very high. The hypervisor has a higher priority than the OS. Based on this, the VMs on the hypervisor can be guaranteed real-time. In particular, embedded hypervisors are more suitable for fields where real-time is important because they make the code lighter, use CPUs, memory, etc. very efficiently, and the HW usage of the hypervisor itself is very small compared to server hypervisors.
-
ContainerContainers are virtualized on top of the OS, so the container operates like an APP on top of the OS. This feature provides good user convenience, but because of this, all library software required for the operation of the APP in the container (especially due to differences in library versions) is included in the container, which increases memory consumption, and because of the structural characteristic of having to go through the OS, the speed is bound to be relatively slow. Also, containers are a type of virtualization technology that is mainly applied at the APP level of a specific OS (mainly Linux OS), so they do not guarantee as much freedom for the OS as hypervisors, and they have a lower priority than the OS kernel, so the OS has priority in the scheduling process. Because of these characteristics, it is difficult for containers to guarantee real-time performance. This may not be critical for general servers, but in embedded systems such as automobile driving functions, real-time performance must be guaranteed and various OSs are used, so it can be a critical problem.
-
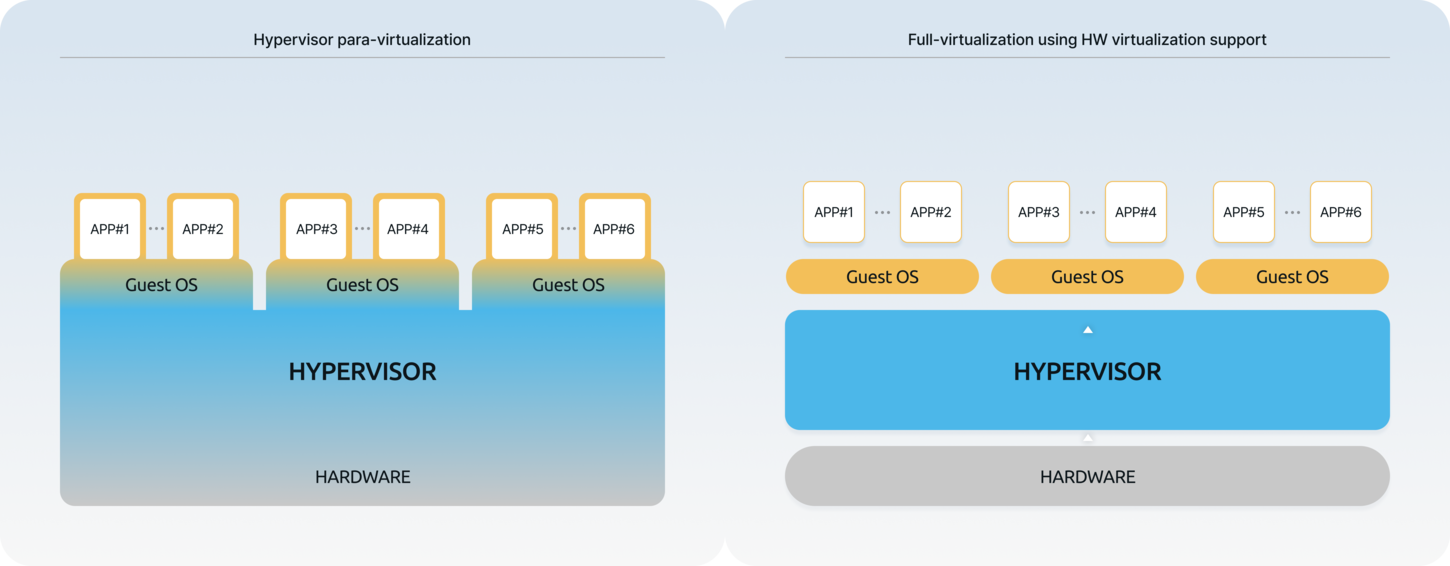
Types of
HypervisorsHypervisors are usually divided into Type 1 and Type 2. In embedded systems where computing hardware resources are relatively insufficient, Type 1, which has a small computing overhead, is mainly used. Type 2 is installed and used as an APP on an existing desktop or server computer OS, so it always requires a Host OS, and the computing overhead is greater than that of Type 1. If you look at Type 1, the hypervisor runs directly on top of the computing hardware, and multiple Guest OSes run on top of it. Therefore, even if a single Guest OS fails to run, the entire system runs stably, and it is an example of a hypervisor system structure with the smallest computing overhead. As such Type 1 hypervisor is suitable for in-vehicle E/E systems. However, as a special case among Type 1, there is a virtualization technique called KVM (where if one of the Guest OSes is a Linux OS, that Linux OS is set as the Host OS, and when the computing hardware is powered on, this Host OS boots first, then the KVM (Kernel-based Virtual Machine) function of the Linux OS is called and operates, and then the Guest OS is called and operates.). In this KVM virtualization method, if there is a problem with the Host OS, Linux OS, the entire system will not operate. As such, in choosing hypervisors, the explanation above should be taken into account. -
Para-virtualizationWhen the hardware to be virtualized (e.g. CPU/MCU) does not have the ability to recognize the hypervisor software privilege mode, it is a method of modifying the hypervisor software and the kernel software of the OS running on it to replace the missing function. It was commonly used in CPU virtualization systems before 2010, but after 2020, even MCU also began to structurally support the mode that recognizes the hypervisor, so paravirtualization is rarely used.
-
Full-virtualizationThe hardware to be virtualized (e.g. CPU/MCU) is provided with the ability to recognize the hypervisor software privilege mode, so that the OS kernel running on top of the hypervisor software can be used as is without modifying the kernel software.

-
Embedded Mobile System Hypervisor and Server HypervisorHypervisors are divided into those for servers (e.g. X86 series CPU) and embedded (e.g. ARM CPU, ARM MCU, Infineon MCU, RENESAS MCU), and although their virtualization structures are similar, the software development methods and hypervisor utilization directions are significantly different. Hypervisors for servers manage massive computing hardware resources and computing scalability, monitor workloads per VM, and dynamically migrate workloads between VMs for workload balancing. They are important functions to cloud computing servers, and are generally developed for the X86 (CISC) architecture, so they are not compatible particularly with those for embedded mobile computing use. On the other hand, embedded hypervisors operate on limited computing hardware resources, must efficiently optimize and manage resources, guarantee real-time performance, and require lightweight code and specialized technologies tailored to RISC architectures such as ARM.


achievable through software
: AEGIS Security Solution
In 2015, an online magazine published an article about two hackers hacking into an SUV from company J, which shocked security experts and users worldwide. This incident indicated that not only future vehicles but also already-released vehicles on the road are at significant risk of hacking.
The risk of vehicle hacking has already become a significant threat to users' lives and property in our everyday lives.
a security hypervisor
-
The first & the best technologyThe beginning of
secure hypervisorsAEGIS is a secure hypervisor solution developed based on experience with the open-source project "Secure Xen ARM." It introduced innovative technology that combines hypervisors and security for the first time in the ARM market.The founder's
deep technical
foundationDr. Suh developed and maintained the 'Secure Xen ARM' open-source project and, together with our development team, built world-class expertise in hypervisor technology. Based on this, we provide market-leading solutions. -
The ultimate security solutionThe importance of
security-by-
designThe importance of security-by-design AEGIS is a hypervisor with security-by-design, fundamentally distinguishing it from traditional hypervisors. This is similar to how earthquake-resistant buildings are designed to endure earthquakes.
-
Diverse and in-depth
security
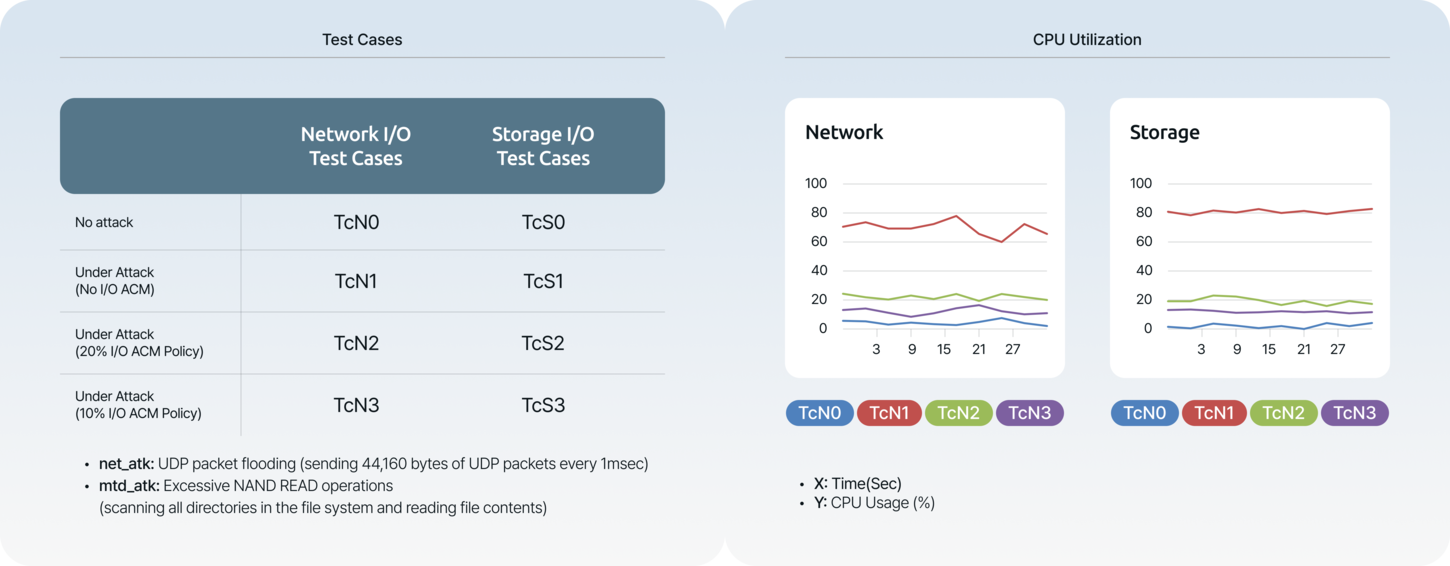
technologiesDiverse and in-depth security technologies AEGIS incorporates diverse and in-depth security technologies and algorithms. One of these is MAC (Mandatory Access Control), which ensures the isolation of each OS. AEGIS ensures stability even during DoS attacks. It maintains security through various technologies while simultaneously guaranteeing real-time performance for each OS and enabling flexible control over OS security. -
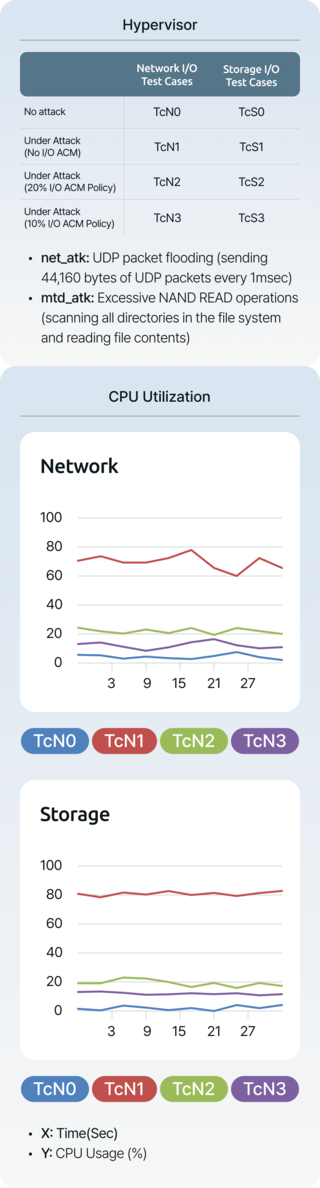
Globally proven technologyIn 2009, AEGIS's foundational technology, based on 'Secure Xen ARM', was validated in a research paper at ACM Mobicom, a global top-tier academic conference. The paper demonstrated AEGIS's capabilities, including effective DoS attack prevention, robust OS security with real-time performance, and flexible security management for OS instances.
-
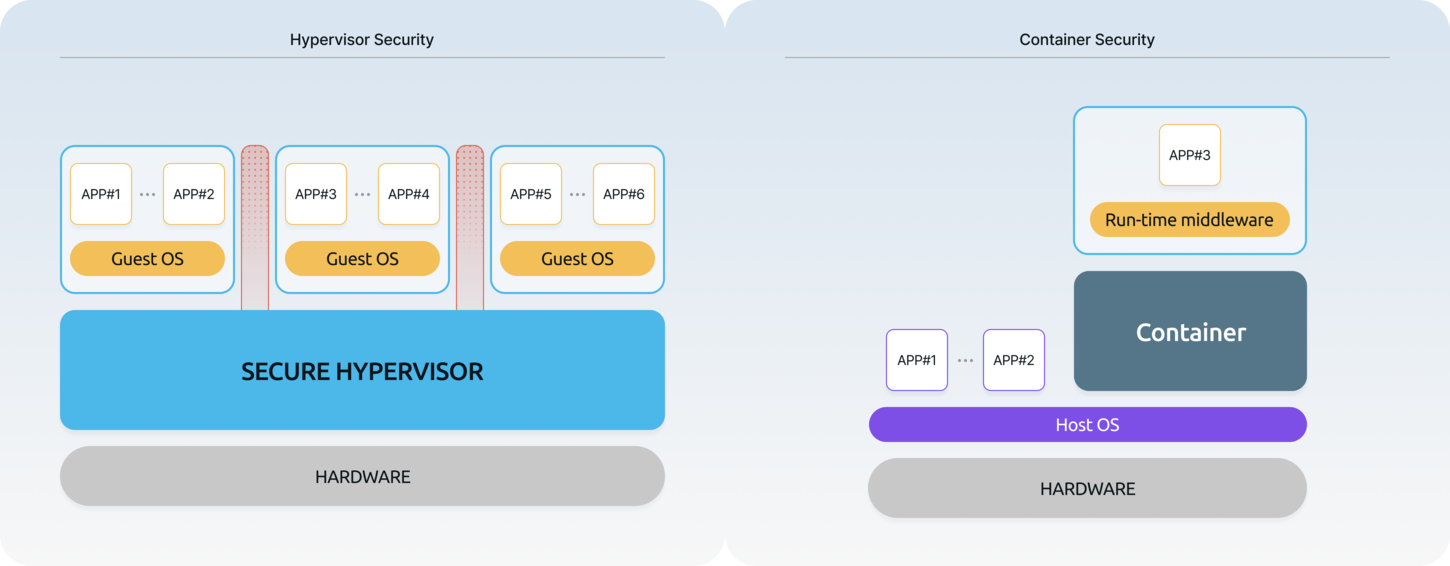
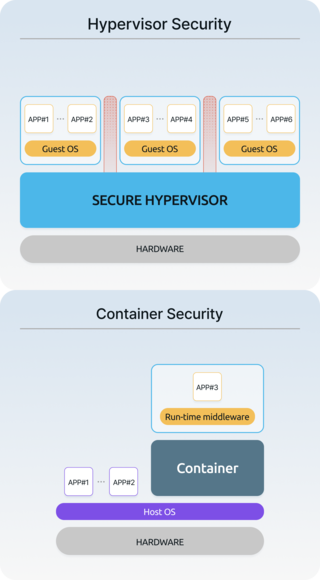
Hypervisor Security
and Container
SecurityHypervisor runs directly on hardware (bare metal) and has higher privileges than Host/Guest OS. Root of Trust is located in hypervisor, so it is highly secure, and it is less exposed to hacking attacks because it does not communicate directly with the outside. Thanks to these characteristics, hypervisor can provide strong security at the level of TrustZone. -
Hypervisor SecurityHypervisors run directly on hardware (bare metal) and have higher priority than the Host OS. With the Root of Trust based on hardware, security is strengthened, and since it does not communicate directly with external entities, it is less exposed to hacking attacks. With these characteristics, hypervisors can provide strong security, such as that of TrustZone.
-
Container SecurityContainer runs on top of the Host OS, so the Root of Trust for security lies with the Host OS. Therefore, if the Host OS is compromised, the container is also exposed to risks, and this issue cannot be fully resolved structurally. Even if the container itself is secure, its security is weakened if the integrity of the Host OS is not guaranteed.
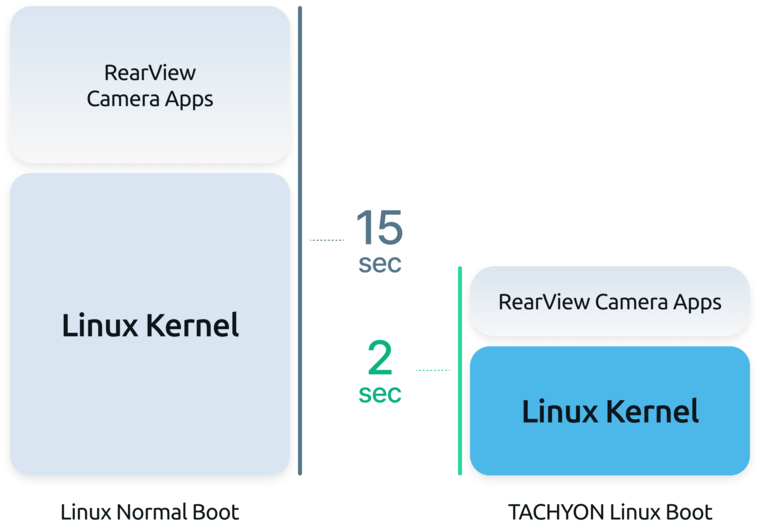
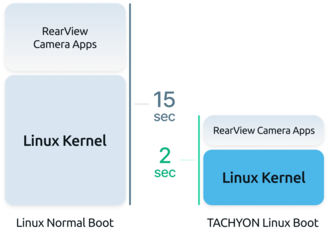
Linux boot process generally exceeds 15 seconds, a duration that is excessively long for some systems.
TACHYON applies a variety of optimization techniques to dramatically reduce the boot time of Linux systems. Over 120 optimization methods are employed in this process, drawing from Perseus's long-standing experience and history in system software design and development.
fast boot solution
reduces the boot time of Linux systems by
applying various optimization techniques.
Introducing the core technologies and the
step-by-step boot process.
-
Power-on and initial hardware initializationBIOS/UEFI
Initialization
(x86-based)When the power is turned on, BIOS or UEFI runs to initialize hardware and inspect boot devices. Fast Boot can shorten boot time by omitting or reducing unnecessary inspections.Boot ROM
(ARM-based)On ARM systems, the Boot ROM takes over the role of initialization and loading the bootloader, replacing the BIOS. While it performs functions similar to the BIOS, its implementation and naming differ due to the architectural characteristics. -
Bootloader loading and executionGRUB
(Grand Unified
Bootloader)As the most widely used multi-boot bootloader, it loads the kernel and initial RAM disk (initramfs) into memory. Optimization of GRUB settings can minimize unnecessary processes.U-Boot (Universal Bootloader)It is the multi-booting bootloader most widely used in embedded systems, supporting hardware initialization, environment configuration, file systems, and network booting. TACHYON achieves fast booting on ARM-based systems through U-Boot configuration optimization.Minimalistic BootloaderBoot time can be further reduced by using a streamlined bootloader tailored to specific environments or requirements. -
Kernel InitializationParallel
InitializationBy initializing as many hardware and loading drivers simultaneously, the overall initialization time is reduced.Asynchronous
driver initializationSome drivers are initialized asynchronously, allowing them to be processed in parallel with other tasks, thereby distributing the boot process efficiently. -
Systemd initializationSystemd-based initializationThe systemd used in modern Linux distributions analyzes dependencies between services and starts as many services simultaneously as possible, enabling faster boot times.Service
OptimizationUnnecessary services and daemons are disabled, and essential services are prioritized during startup to improve boot speed.
-
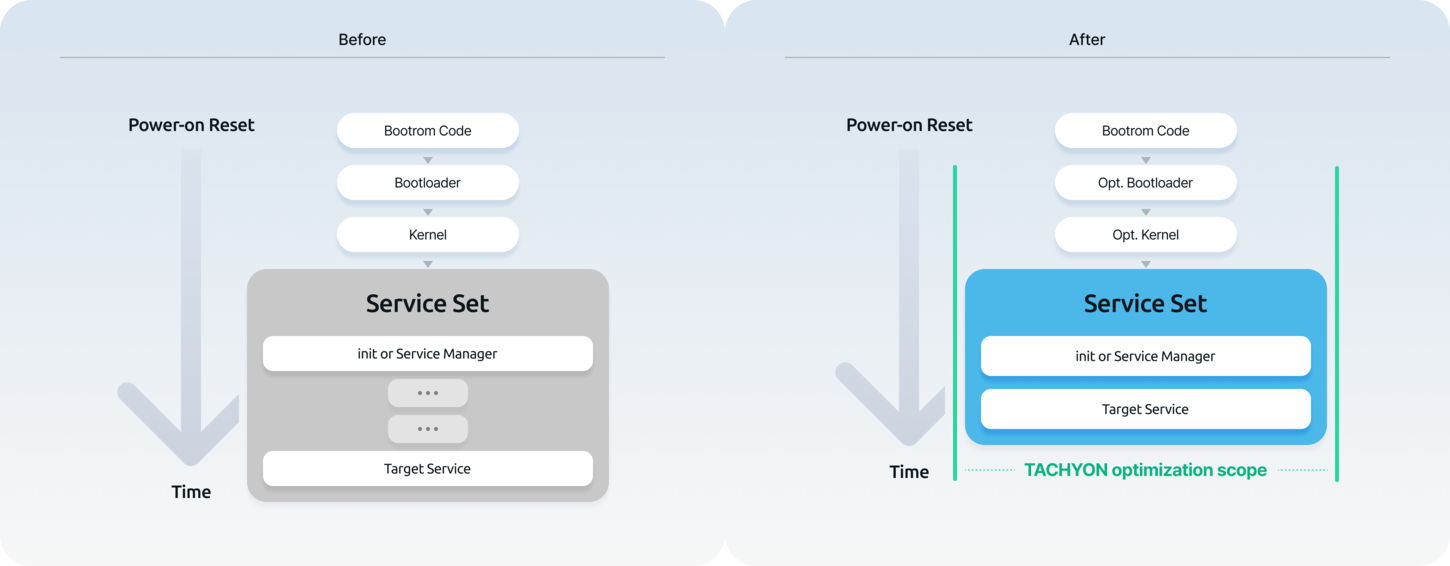
TACHYON solution, the definition of Boot Time
-
After power-onThe boot time is defined as the time taken until the completion of the startup of the customer-specified service sets or the readiness of the execution environment (reflecting customer requirements)
-
After Boot Time OptimizationEnsuring the operational stability of all functions used by the target system
-
Ultra-fast boot
solution across
various architectures.TACHYON can operate across various architectures, such as x86 and ARM, optimizing the entire process from bootloader to kernel initialization, lightening of the root file system and service execution, delivering an astonishingly fast boot time. By integrating efficient hardware initialization, parallel process execution, and service optimization techniques, TACHYON delivers excellent performance across a wide range of applications, from embedded devices for example vehicle and mobile, even further to desktop computers.
about our technology.